Smart grids are cyber-physical systems whose primary goals include the protection of privacy and confidentiality of information, systems, users, and all related assets. The core of this goal heavily relies on Advanced Metering Infrastructure (AMI), which collects, measures, analyzes, and transmits the electric energy consumption data to the central collection facility. In the smart grid, enhanced metering devices or smart meters take care of the basic AMI tasks and relay the information to operators through a network connection. It is one of the core enablers of a smart grid that takes care of distribution and billing tasks seamlessly. Thus, data security and deployment of smart grids heavily rely on AMI protection. For instance, any fault with AMI control functions can compromise the integrity of the complete network and every smart meter.
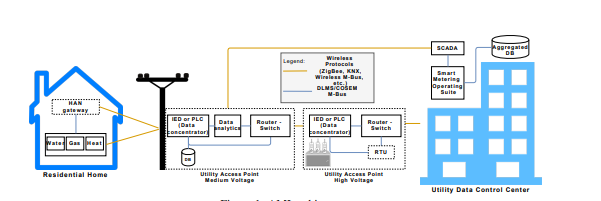
Figure 1: Graphical Presentation of Advanced Metering Infrastructure
Safeguarding Smart Grids: Advanced Approaches To Ensure Data Security
Similarly, protecting metering is crucial as it contains users’ data, such as voltage quality data, utilities, energy usage patterns, and much more, making it privacy-sensitive. The users may need to share that data with other entities like insurance or advisory companies, which creates loopholes for data leakage. These loopholes include smart meter ports, data inference during transmission through methods like Non-Intrusive Load Monitoring, and energy consumption profile extraction through smartphone applications via real-time monitoring methods.
As 5G technology rolls in, it brings two key features: ultra-reliable and low-latency communication (uRLLC) and machine-type communication (MTC). Machine-type communication on 5G networks supports several smart grid processes. It includes low latency, integration of DERs, vehicle-to-grid (V2G), smart metering, handling high data volumes, and fault localization. However, data security is still a vulnerable point with this tech, which further necessitates the requirement for better standards and protocols.
Several other such data security challenges need to be acknowledged and countered through advanced solutions. This blog sheds light on some of the most advanced approaches that hold great potential to resolve major concerns regarding the data security of smart grids.
Most Advanced Data Security Measures For Smart Grids AMIs
Secure Communication Protocols:
Secure communication protocols can safeguard AMI from remote attacks. The most successful protocols offer end-to-end security with additional layers in protocol stacks like authentication and encryption. For instance, the standard de facto protocols are DLMS/COSEM, which provide encryption and authentication. Similarly, M-bus is a basic standard used across Europe, and it is utilized for remote electricity, gas, etc. meters for billing. The most advanced protocol is the IEC 61850, which was introduced to replace DNP3 for substation communications.
Currently, power substations have restricted their usage, but in the near future, they will be employed for all external substation communications. For now, the UCA international user group has established the Advanced Metering Infrastructure System Security Requirements (AMI-SER) for AMI security in smart grids across the globe. Here is a summary of the most advanced smart grid security standards and protocols that impact AMI security around the world:
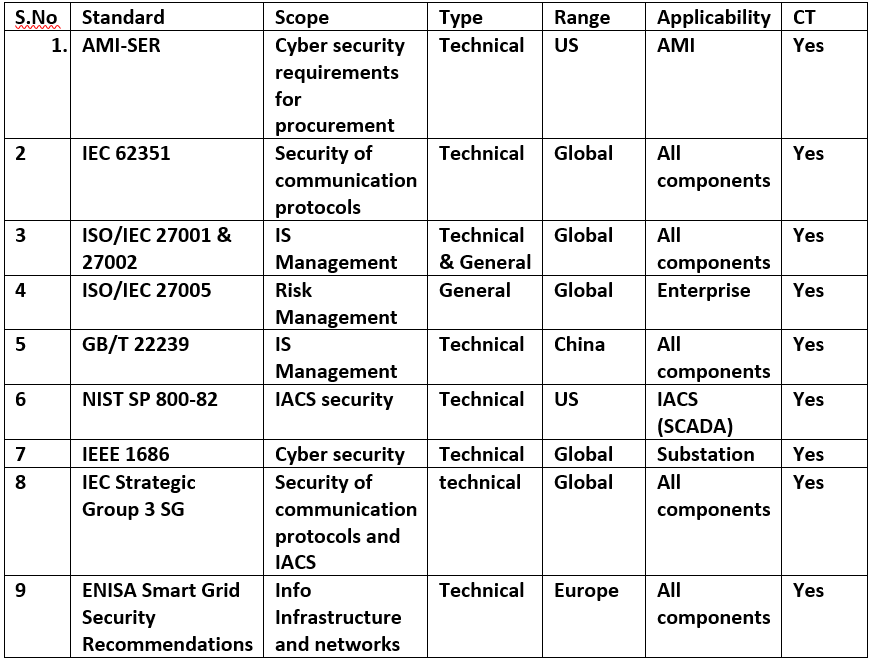
Figure 2: Major Smart Grid Data Security Protocols and Standards Across The Globe
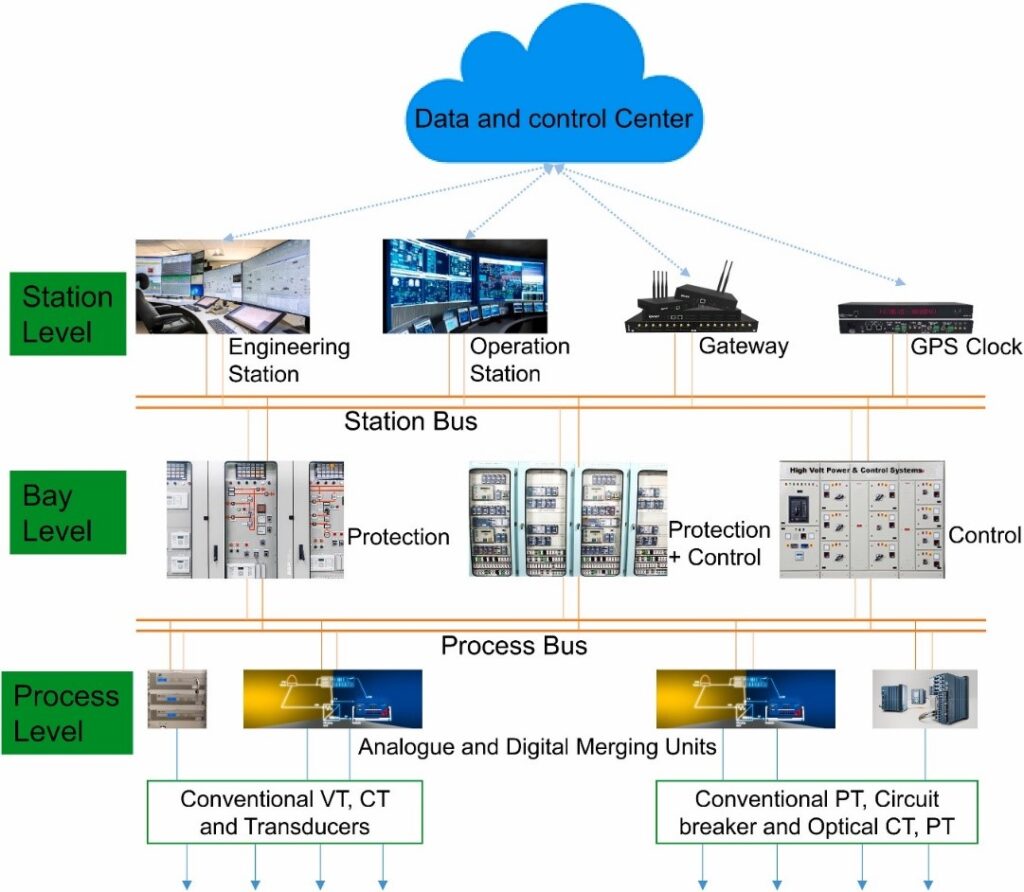
Figure 3: IEC 61850 Substation Automation System Communication Architecture
Unified Security Measures:
Simultaneous applications of different safety measures, such as network monitoring solutions, encryption, authentication, and supervisory systems like SCADA or Data Analytics, can and will play a key role in securing smart grid AMIs. Alongside, there exists an imminent need to acknowledge indicators of suspicious behavior. It additionally requires dedicated incident investigation and scoping to differentiate genuine causes of concern from false positives. The investigation findings are used to set up advanced firewalls, prevent unauthorized access, and secure smart grid assets.
Better Regulatory Framework:
End-users’ lack of precaution about these issues can easily compromise the AMI data, even with encryption. Adversaries can easily subject most users’ shared keys to inference and access. Regulatory frameworks are necessary to prevent unwanted access to users’ data. For instance, the General Data Protection Regulation (GDPR) has mandated data collecting online services in Europe. It informs users about the data collection methodologies and gets their consent. They also need to ensure that data storage is in a secure location. Moreover, they share it with third parties within defined time frames.
Data Loss Prevention Techniques:
Data encryption is one of the essential Data Loss Protection (DLP) techniques used in smart grids. Alongside encryption, implementing other measures like Role-based Access Control (RBAC), strong password policies, Multi-Factor Authentication (MFA), intrusion prevention systems (IPS), intrusion detection systems (IDS), data backup, and disaster recovery mechanisms is crucial to prevent data loss and enhance overall grid security. By combining these techniques, smart grids can better safeguard against potential data breaches and ensure the integrity of their data. The only basic prerequisite is the holistic implementation of the techniques while tailoring them for smart grid employment.
Blockchain:
Applying blockchain technology and smart contracts to AMI security adds new blocks to each transaction. This enhances the overall security of the system. AMIs contain information concerning energy consumption, payment records, and billing. Moreover, we can add specific conditions to prevent one-point failure in the smart grid system. It can be related to smart grid security or the contract on energy generation, distribution, and remote monitoring fronts. Blockchain is one of the most sure-shot ways to ensure all participants’ privacy and AMI data. Recent research proposed a reliable energy scheduling model through smart contracts and blockchain. It can help address the rising privacy concerns for a centralized system to handle behavioral and financial information.
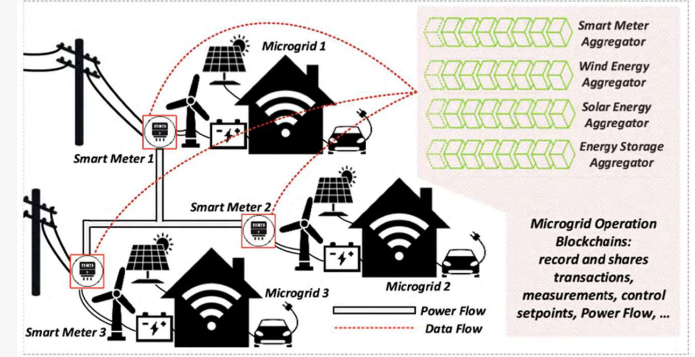
Figure 3: Blockchain For Advanced Metering Infrastructure Data Security
AI and ML:
Artificial intelligence and machine learning techniques can analyze high volumes of data, patterns, and anomalies in much less time. AMI also enhances security, speeds up threat response, offers better intrusion detection, and automates incident response.
Final Word
AMI is the backbone of smart grids. Compromising on it can lead to far-reaching consequences for every connected smart meter and the complete network. The standards mentioned above and protocols can also potentially maintain the integrity and confidentiality of smart grid assets and users. Security measures will continue to evolve due to the ever-evolving nature of threats and technologies. The implementation of advanced data security protocols like IAC AMI-SER will also play a crucial role in ensuring better performance. These measures aim to enhance smart grid systems’ overall security and efficiency.