Cybersecurity in a connected vehicular environment involves shielding vehicle control units, networks, and sensitive data from cyber threats like malware, hacking, data tampering, etc. Our most recent report dives into the critical role of automotive cybersecurity and the breakthrough notion of the Digital Twin—a dynamic, digital copy of physical car systems.
This in-depth examination not only highlights the complex challenges confronting automotive cybersecurity in the face of escalating cyber threats but also demonstrates how leveraging Digital Twins can provide unparalleled insights into threat detection, system vulnerabilities, and real-time response strategies.
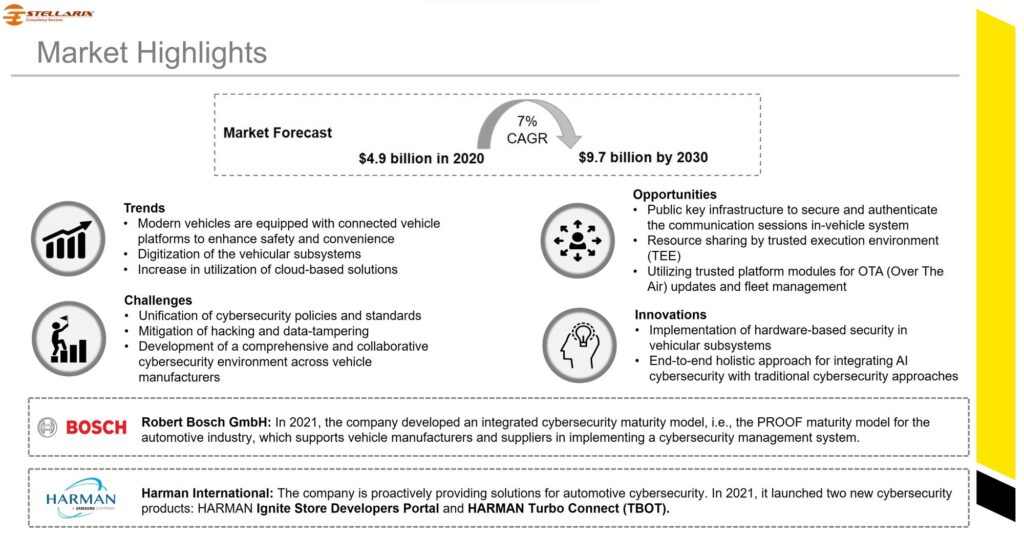
The automotive cybersecurity market is anticipated to reach $9 billion by Year 2030.
Cybersecurity is not new to automotive. However, mass-scale commercialization of the same has yet to take the desired pace, adding an enormous scope for future research. The following are a few examples of vulnerability (attack vectors) & associated areas of the research:
Attack Vectors & Attack surfaces:
- In – vehicle Communication:
- Intra vehicle communication
- Sensors
- ECUs
- Booting and OTA updates
- Vehicle-to-everything (V2X) communication
- Vehicle to vehicle (V2V)
- Vehicle to Infrastructure (V2I)
- Vehicle-to-Home(V2H)
- Vehicle to IoT (V2IoT)
Research Scopes:
- Research Scope I – Federated learning can be implemented to mitigate privacy concerns and data tampering issues.
- Research Scope II – A trusted execution environment (TEE) can be incorporated into vehicles to provide a platform for secure booting and OTA updates.
- Research Scope III – Privacy-Preserving authentication using blockchain with anonymous Identity in Vehicular Networks.
- Research Scope IV – Keyless entry (biometric authentication on encrypted data) can be incorporated into autonomous vehicles to enhance security.
- Chapter 1: Automotive Cybersecurity Market Overview
- Notable Collaborations in Automotive Cybersecurity
- Attack Types & Mitigation By Major OEMs
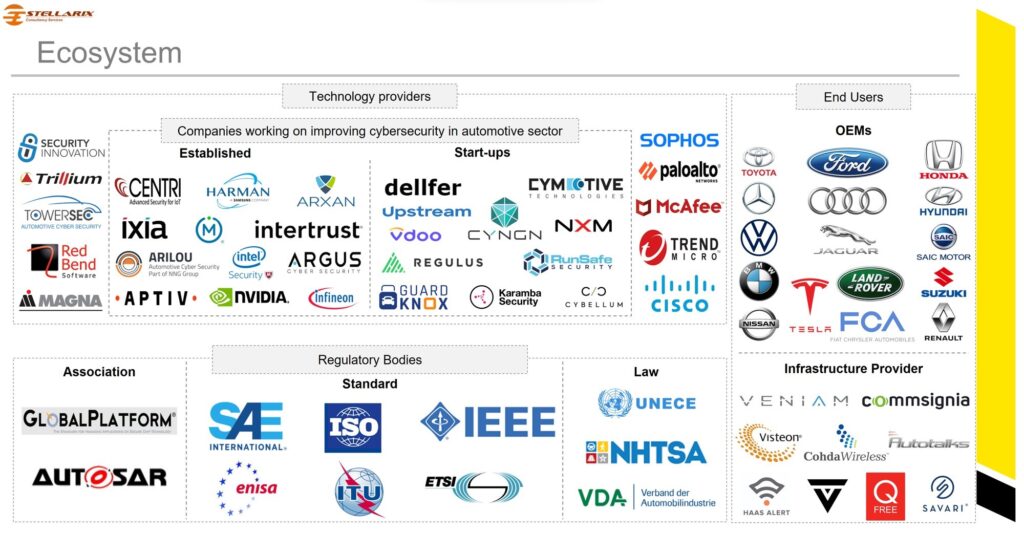
- Ecosystem
- Cybersecurity Models by Key Competitors
- Challenges & Potential Research Opportunities
- Integration of federated learning in vehicular network
- Trusted execution environment in automotive vehicles
- Privacy-preserving authentication using Blockchain
- Biometric-enabled keyless entry
- Chapter 2: Digital Twin
- Key Enabling Technologies
- Use Cases & Key Players
- Key start-ups working on Digital twin in the Automotive Industry
- Key Collaborations: Solution Providers & OEMs
- Case Study on Digital Twin in Cybersecurity