As we transition toward the Quantum Cryptography and Computing era, the basic foundation of digital security is at risk. This is due to the vulnerabilities of existing cryptographic algorithms, which future quantum computing algorithms will exploit.
Hence, a competent, highly efficient algorithm is required to manage these services and applications, especially for highly data-sensitive applications such as financial services. Such algorithms are termed Quantum Cryptography, which is immune to threats arising from quantum computing.
This article explores Quantum Cryptography, highlighting the differences and technical advantages that Quantum Cryptography has over traditional cryptography. Additionally, the challenges of Quantum Cryptography usage and implementation, the market activities, and others.
What Is Quantum Cryptography? How Does It Differ From Traditional Cryptographic Algorithms?
Quantum Cryptographic methods, which utilize quantum mechanics principles for data transmission and encryption applications, prevent access by traditional as well as quantum computing-enabled malicious entities.
Public key cryptography algorithms such as Elliptical Curve Cryptography (ECC), Digital Signature Algorithm (DSA), Rivest Shamir Adleman (RSA), and Diffie Hellman algorithms are asymmetric cryptography. This is because they use pairs of public and private keys for encryption and decryption. However, they are heavily reliant on discrete logarithms and integer factorization. They are vulnerable to quantum algorithms such as Shor’s algorithm.
Symmetric cryptography employs a single key for both encryption and decryption. Notable examples include the Advanced Encryption Standard (AES), Data Encryption Standard (DES), and the Blowfish algorithm. However, symmetric cryptography has some drawbacks, such as heavy reliance on the computational hardness of mathematical problems.
All of these drawbacks can be addressed with Quantum Cryptography. Quantum Cryptography can be asymmetric or symmetric. However, it is different from classical cryptography, such as the ones mentioned above, as it uses quantum phenomena.
For example, Quantum Key Distribution (QKD) generates and shares secret public and private keys between two parties. Hence, it could be an example of asymmetric cryptography. However, QKD does not encrypt/decrypt messages; it only provides keys for doing so with a symmetric encryption algorithm.
Another Quantum Cryptography method, Quantum Secure Direct Communication (QSDC), transmits secret messages without needing a pre-shared key. Hence, it can be seen as an example of symmetric cryptography. However, QSDC does not use a conventional key but uses a quantum state or a quantum entanglement.
Applications
In the future, quantum computers will have the potential to break all the currently available secure communications. Hence, quantum cryptography will see wider adoption in the financial sector to secure confidential information such as financial transactions. Other industries where quantum cryptography will be utilized are satellite communication, data centers, and media. Some of the following types of quantum cryptographic methods will be used for digital security applications:
- Quantum Key Distribution (QKD): QKD is a protected communication method that allows the secure distribution of secret keys that can be accessed only by authorized parties. It enables two users to detect interference by a third party trying to obtain the key.
- Mistrustful Quantum Cryptography: This type of quantum cryptography is used when the certainty and trustworthiness of the other party are low. It uses quantum measurements and quantum entanglement to ensure that both parties do not gain advantages over each other or cheat each other
- Device-independent Quantum Cryptography: This type of quantum cryptography uses Bell’s inequalities and quantum nonlocality. It ensures task completion without device imperfections and specifications. It does not rely on the functionality or trustworthiness of the devices used to implement quantum cryptography.
- Quantum Coin Flipping: This cryptographic primitive is also used when the level of trustworthiness between two parties is low, thus reducing the bias of dishonest players. It uses the transmission of qubits, allowing participants to communicate via a quantum channel and share information.
Components Of Quantum Cryptography
A few technologies and solutions that aid in successfully implementing Quantum Cryptography are described below.
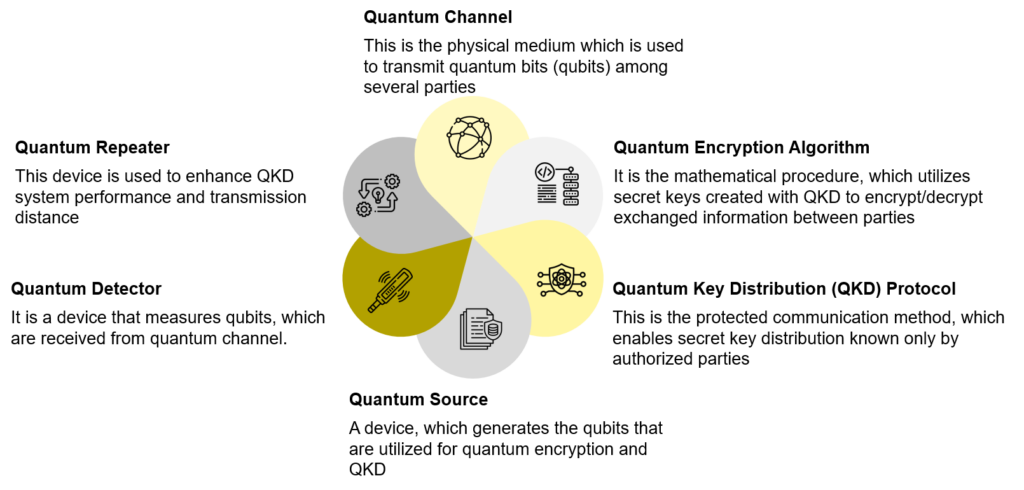
Figure: Components of Quantum Cryptography
Key Player Activities
- To achieve secure and reliable communication in the era of quantum computing, communication service providers (CSPs) need to implement Quantum Cryptography solutions. These solutions can protect their data and networks from quantum attacks. Players are developing and deploying various quantum technologies to enable the CSPs to provide end-to-end quantum security. These include QKD, quantum encryption, and quantum networks.
- In November 2023, SK Telecom implemented QKD systems at Equinix’s SL1 data center in Sangam-dong, providing long-term data security and quantum security to end users of the data center
- In September 2023, Honeywell partnered with Aegiq to create a QKD solution for small satellites. The collaboration will combine Honeywell’s atmospheric sensing technology and Aegiq’s emulation toolkit to link the performance of optical communication technologies used by small satellites
- In July 2023, QuantLR and PacketLight Networks announced the successful integration of QuantLR’s QKD services with PacketLight’s Optical Transport Networking (OTN) encrypted transport to achieve quantum secure encrypted network
Challenges With Quantum Cryptography
Quantum Cryptography has certain advantages over traditional cryptographic techniques. It includes detecting eavesdropping on quantum channels, which will help identify intruders. However, despite its various advantages, Quantum Cryptography is at a very nascent stage. Also, its wider adoption will require a greater amount of research and development. The main challenges for Quantum Cryptographic methods are listed below:
High Cost:
Quantum Cryptography requires specialized hardware, such as quantum detectors, repeaters, and sources. Hence, it entails a higher capital expenditure compared to traditional symmetric cryptography.
Semi-substitute:
It does not perform encryption and decryption. Instead, Quantum Cryptography only serves key distribution. Hence, secret keys still need to be used with a traditional symmetric cryptography algorithm for data encryption and decryption. Therefore, Quantum Cryptography does not entirely substitute traditional symmetric cryptography but complements it.
Transmission Distance:
Quantum Cryptography depends on sending a single photon or entangled pairs of photons over free space or an optical fiber. However, photons are subject to noise and loss that limit the data rate and transmission distance over a distance.
Device Security:
Certain vulnerabilities or imperfections, such as emitting multiple photons instead of a single one by the source or external signals obstructing the reception path of the signal while quantum detectors capture it, can compromise the system’s security.
Standardization And Interoperability:
Quantum Cryptography still lags behind widespread adoption due to the lack of acceptable and available protocols and standards. Various quantum cryptographic schemes, such as E91, CV-QKD, and BB84 that use varying quantum states, security proofs, and encoding methods are available. The integration of Quantum Cryptography with legacy communication networks and classical cryptography also needs a high amount of work to achieve high interoperability
All the above challenges are highly complex but must be addressed to ensure that these solutions are delivered with the highest quality, regardless of the technology’s complexity and novelty, as the payoff is very high.
Also, due to the above challenges, the key bodies in the US responsible for setting strategy and tone, namely the National Institute of Standards and Technology (NIST) and the National Security Agency (NSA), have taken a different stance to support post-quantum cryptography (PQC). Until the above challenges are resolved, these bodies view PQC as a more cost-efficient and easy-to-maintain solution than Quantum Cryptography. Even after these challenges, the issues highlighted by NIST and NSA have since been corrected. Players are projecting that the existing in-ground fiber infrastructure is sufficient to support QKD solutions, which require this infrastructure to function.
Conclusion
Quantum Cryptographic methods have been a cornerstone of future security solutions’ success. Moreover, they will continue to evolve and play an even more vital role as we transition into the era of quantum networks. The seamless integration of diverse quantum technologies and their security advantages position Quantum Cryptography as a critical tool for delivering the promise of secure, reliable, and scalable quantum communication. As technology progresses, quantum cryptographic methods will remain at the forefront. It will ensure these networks operate effectively and efficiently, connecting the world like never before.