Mitigation Techniques of Side Channel Attacks
Cybersecurity has become essential in the rapidly evolving technology landscape for information sharing. However, a new type of attack, known as the side-channel attack (SCA), has emerged. It exploits unintentional information leakage from sources such as power consumption, electromagnetic emissions, and timing fluctuations. These leaks compromise sensitive data, including encryption keys and passwords, and even bypass robust cryptographic algorithms. Thus, there is an increasing demand for countermeasure techniques to mitigate these attacks. A lot of enhancements in the cryptographic algorithms to minimize information leakage and enhance system resilience against side-channel attacks are driven by advancements in hardware-based security solutions and software techniques. The article explores the complexities of side-channel attacks, various types, and potential strategies to mitigate their impact. Also, it focuses on the vulnerable use cases and the prominent players mitigating solutions, if any, prevailing in the market.
What are Side-Channel Attacks?
A side-channel attack, also known as a sidebar attack or an implementation attack, is a security breach that gathers information either from the system’s execution process or by process manipulation. These attacks are based on observing and analyzing the physical behavior of encryption systems during cryptographic operations. These attacks aim to extrude sensitive information, including cryptographic keys, by measuring simultaneous hardware emissions. It can occur in electromagnetic, acoustic, power, optical, timing, memory cache, hardware-related, and other ways. For example, an attacker can measure the device power consumption engaged in encryption or decryption processes. Thus, it can leverage statistical techniques to deduce the secret key or plaintext. Alternatively, an attacker can introduce faults or errors in the encryption system by manipulating the voltage, temperature, or clock frequency. Thus, it can exploit the resulting anomalies to reveal the secret information.
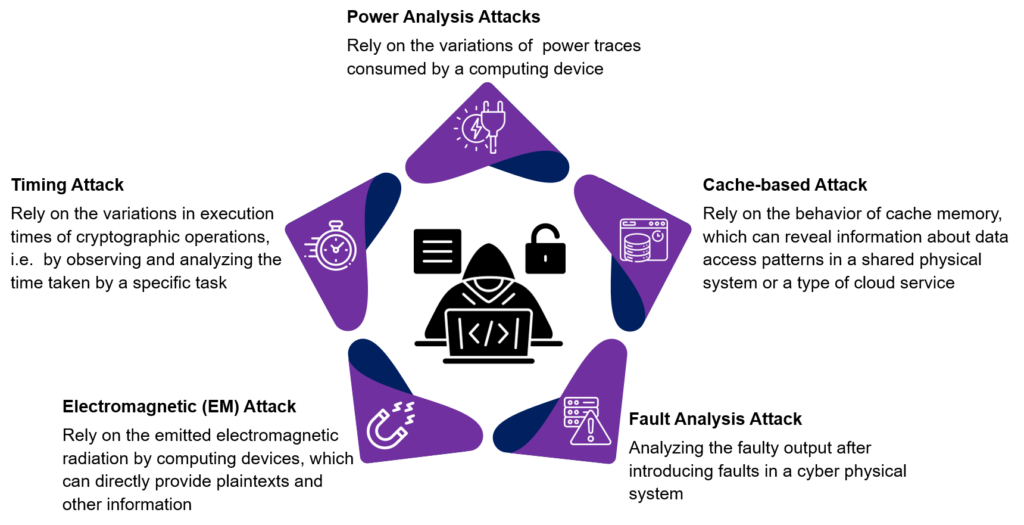
Figure 1: Prominent Types of Side-channel Attacks
Significance of Mitigation Techniques of Side-Channel Attacks
The figure below discloses some of the prominent countermeasures against the side-channel attacks. They are using constant-time algorithms, injecting noise, partitioning time and hardware, performing regular security audits, masking, and blinding, temporal desynchronization, isolating processes and virtual machines, countermeasures for power and electromagnetic radiation analysis, employing white-box cryptography, implementing differential power analysis (DPA) resistance, randomizing operations, implementing secure hardware designs, using side-channel-resistant implementations, circuit redesigning, integrating real-world testing and others.
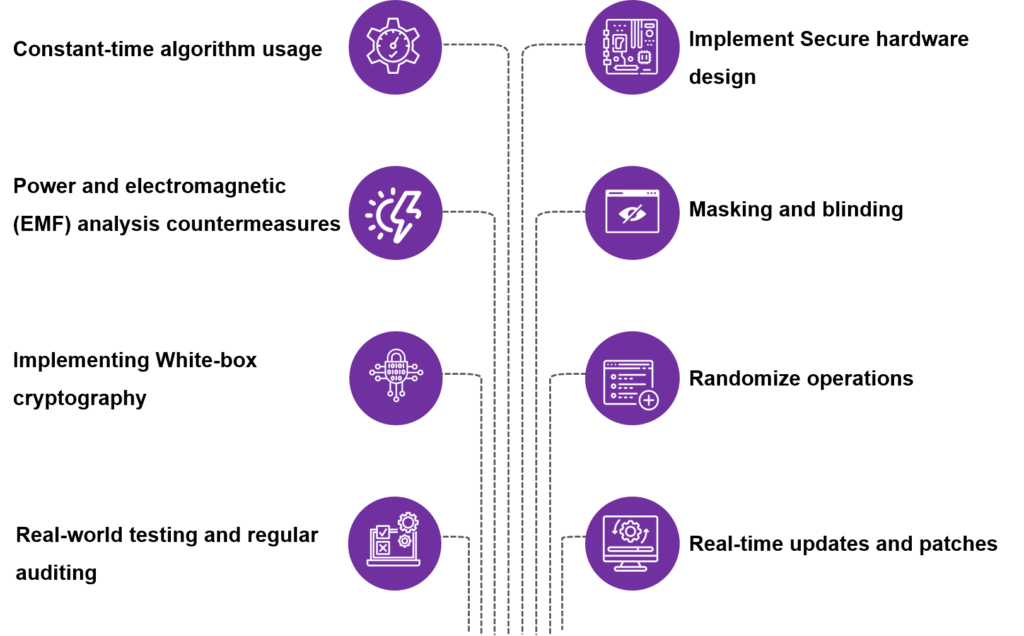
Figure 2: Prominent Mitigation Techniques for Side-channel Attack
Key mitigation techniques are explained below in brief:
Hardware Level Mitigation Techniques
- Implement Secure Hardware Design: At the hardware level, design logic gates, circuits, and silicon layouts to reduce physical leakage. This is done by utilizing tamper-resistant chips or shielding sensitive signals in a silicon layout through the judicious routing of metal layers.
- Introducing Power and Electromagnetic (EMF) Analysis Countermeasures: Introducing dynamic voltage variation randomly, utilizing displays with special shielding effects to reduce EMF emissions, and employing power analysis counters, such as power gating, balancing power consumption, altogether make it challenging to correlate current consumption with logical operations directly.
- Real-World Testing and Regular Auditing: Evaluating cryptographic devices under real-world conditions, such as environmental factors and power fluctuations, or conducting regular security audits or assessments
- Some other techniques that can be implemented into the hardware are physically unclonable functions (PUFs), physically random functions (PRFs), or performance counters.
Software Level Mitigation Techniques
- Randomizing Operations: Introducing random operations, such as an unexpected delay, algorithmic noise, changing the data access patterns, or implementing dummy instructions into their code, makes it difficult for attackers to correlate side-channel information with specific data or keys.
- Constant-Time Algorithm Usage: Utilizing algorithms that exhibit consistent execution times, ensuring their processing time remains independent of the data they handle or the secret key in use.
- Cryptographic Algorithms Integration: Integrating the masking, hiding, or blinding technique to confuse or manipulate the sensitive data in cryptographic operations by introducing masks to the data, differential power analysis (DPA) resistant cryptographic algorithms, or by implementing the white-box cryptography technique where cryptographic algorithms and keys can be transformed so they remain secure.
- Cache Partitioning Strategy: Ensuring strong isolation between different processes or virtual machines or isolating cache resources utilized by various applications or users can limit the effectiveness of cache-based attacks and mitigate potential leaks.
- Real-Time Updates and Patches: Keeping the software, firmware, and hardware up-to-date with the latest security patches can help address known vulnerabilities and reduce the risk of successful side-channel attacks.
- Transforming Software Design: Design the software to be isochronous, i.e., to run the software for an exactly constant amount of time, independent of secret values.
The mitigation techniques can be further strengthened by incorporating the AI-based algorithm, as it simplifies the identification of side-channel leakage. Additionally, this is achieved by strategically distorting the attacking algorithms used by the attacker at precise moments.
Side-Channel Attack Vulnerabilities Use Cases
The side-channel attacks lead to the theft of sensitive data and the exploitation of information leakage from a system. Thus compromising its security and affecting the trust of businesses, consumers, and the overall market. Below are some of the real-world examples of SCAs to learn how they exploit the systems:
Side-Channel Attacks on CPU:
In August 2023, cybersecurity researchers discovered a trio of side-channel attacks that could affect or exploit modern CPUs to leak sensitive data. These newly disclosed security vulnerabilities leverage AMD’s Zen 2 architecture-based processor known as Zenbleed.
- Collide + Power: This is a power side-channel vulnerability in AMD and Intel processors that allows theft to monitor the CPU power consumption as the data in a cache line changes over time. Hence, this results in a leak of sensitive information.
- Downfall: This allows attackers to violate the software-hardware boundary established in modern Intel CPU processors by exposing passwords, encryption keys, and private data such as banking information, personal emails, and messages through a micro-architectural state or via local access.
- Inception: This allows an attacker to influence the return address prediction. This transient execution attack leaks arbitrary kernel memory on all AMD Zen CPUs, including the latest Zen 4 processors.
Spectre based on Linear Address Masking (SLAM):
This new side-channel attack type, SLAM, exploits Intel, ARM, and AMD CPUs. Based on Spectre Branch History Injection (BHI) attacks, the attack leverages a memory feature of CPUs and circumvents hardware protections. It exposes kernel-memory passwords by allowing the software to use untranslated data bits in 64-bit linear addresses to store the kernel metadata by extracting encryption keys and root passwords.
Side-Channel Attacks on Graphics Processing Units:
Researchers from the University of Texas, Carnegie Mellon University, University of Washington, and the University of Illinois have discovered a new type of SCA that exploits all modern GPUs to obtain sensitive information. Moreover, it leverages graphical data compression, an optimization technique designed to improve performance in modern GPUs. The GPUs from AMD, Apple, ARM, Intel, Nvidia, and Qualcomm are vulnerable to this new type of SCA.
Side-Channel Attacks on Shared Micro-architectural Structures:
This allows attackers to access the sensitive information related to Shared Micro-architectural Structures to access sensitive information. Researchers from the Massachusetts Institute of Technology (MIT) have devised a framework. It allows a comprehensive side-channel leakage evaluation of active attackers, real victim applications, and mitigation techniques for the amount of data leaked through these attacks.
IP Data Analytics of SCA
Several companies are actively filing patents in the SCA domain. They want to establish their market presence by enhancing their security measures and staying ahead of potential threats. SCA patents focused on innovative methods to mitigate side-channel vulnerabilities. It includes secure algorithms, advanced cryptographic techniques, hardware-based countermeasures, and others. The figure below shows the top 10 key players in side-channel attack mitigation
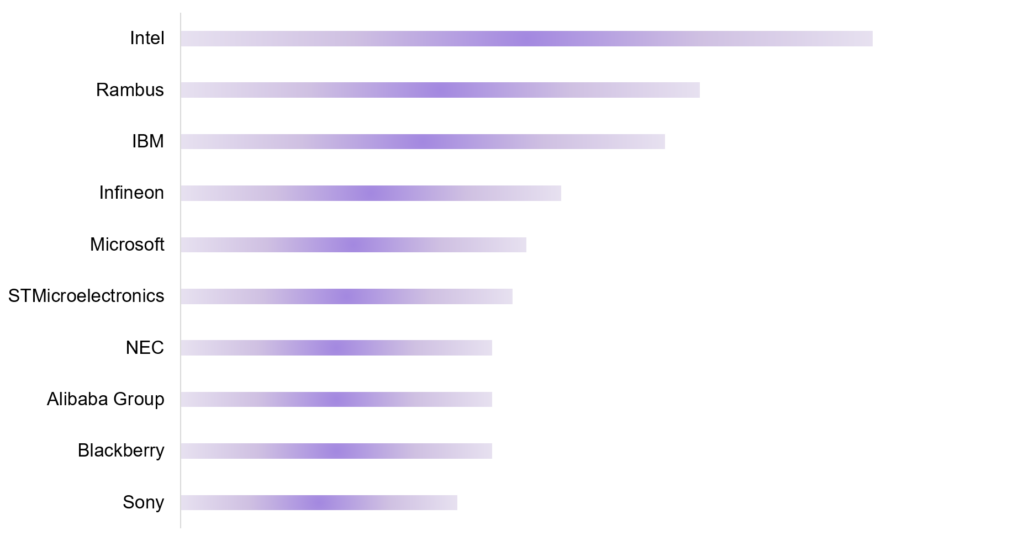
Figure 3: Key Players Patent Volumes Related to Side-channel Attack Mitigation
How DeepSeek Can Help in Mitigating Side-Channel-Attacks?
The impact of DeepSeek on operational practices and architecture on mitigation techniques of these attacks can be analyzed through several key aspects.
- The integration of AI-driven real-time monitoring systems can significantly bolster defenses against side-channel attacks
- By using DeepSeek, industries can develop adaptive security measures that respond dynamically to detected anomalies in system behavior
Conclusion
The continuous development of mitigation strategies for side-channel attacks has become vital. This is due to the increasing number of new types of sophisticated attacks. They leverage unintended information leakage from computing networks. The enhancement in the mitigation techniques focuses on detecting and preventing side-channel attacks on hardware and non-hardware or software levels. It uses a variety of countermeasures, such as integrating randomized operations. Moreover, algorithmic noise or delay in the information data can be caused by using temper-resistance chips, masking or hiding techniques, and others. Still, many improvements need to be made to enhance these prevailing mitigation techniques or develop new mitigation methods because these attacks will not be stopped in the near future.



