Cybersecurity in Software-Defined Vehicles (SDVs): Protecting Data in a Connected World
The scope of protecting resources expanded as society evolved in pace with industrial and technological advancements, encompassing not only physical goods like food, housing, and money, but also intangible assets such as data, the cloud, and even blockchain. As technology advances, implementing connectivity in complex systems, such as transportation and mobility, is becoming increasingly important. This is causing a shift in the automotive industry as it drives towards completely self-governing, software-driven vehicles.
A software-defined vehicle (SDV) is one whose features and capabilities are primarily enabled through software; the software will be used increasingly to provide features such as automation, connectivity, and personalization.
SDVs are expected to account for 90% of all auto production by 2029, as consumer demand continues to rise. However, the growing need for SDVs also raises unforeseen cybersecurity risks.
The Rise of the Software-Defined Vehicle
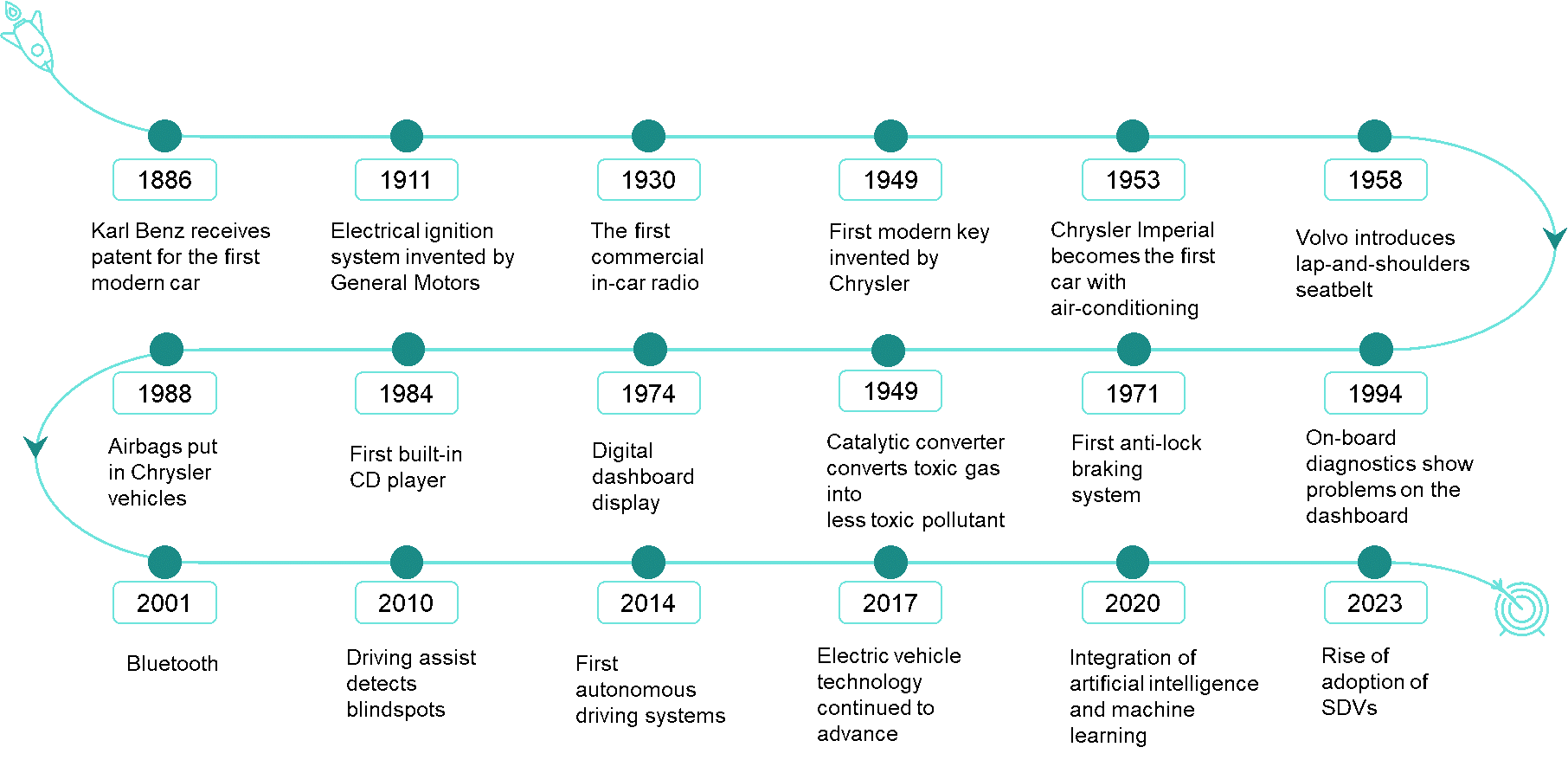
The automobile industry has grown into a dynamic and vibrant sector over time. As demand for cars increased in the 20th century, new features and technologies were introduced, including radios, key fobs, electric vehicles, internet-connected cars, and software-defined vehicles.
With this supercomputer on wheels, it was only a matter of time before cars became connected. A connected vehicle links to the internet, communicates, and shares data with other devices or systems. Later, the concept of self-driving cars gained prominence. With connectivity, more features emerged, such as Vehicle-to-Everything (V2X) technology, enabling the vehicles to connect and communicate with other vehicles, infrastructure, and networks. This technology opens new opportunities for the automotive sector.
As car technology continues to evolve, a significant and new scope has emerged: “Software-defined Vehicles.” These are vehicles that utilize software to power features such as ADAS and infotainment.
- Connectivity Advancements: Wireless technologies like Wi-Fi, Bluetooth, and mobile networks have played a crucial role in helping devices and systems to stay connected effortlessly. These connectivity advancements are enabling data collection and analysis in real-time, even from challenging and remote locations.
- Sensor Technology: The miniaturization and price decrease of sensors have played a crucial role in the expansion of IoT. Sophisticated sensors that can detect temperature, pressure, humidity, vibration, and other variables are now integrated into various industrial machinery, facilitating real-time monitoring and predictive maintenance.
- Data and Analytics: The capability to gather and assess vast quantities of data from IoT sensors and devices has resulted in the growth of data analytics. Analytical techniques, like artificial intelligence (AI) and machine learning (ML), offer rapid insights, predictive maintenance, and improvements in manufacturing processes.
Edge computing addresses the challenges of centralized computing, such as latency, bandwidth, data privacy, and autonomy, by moving processing closer to where data is generated—devices and users. This shift reduces internet load, minimizes latency issues, speeds up response times, lowers security risks, improves application performance, provides deeper insights, and enables essential data analysis, all of which lead to better customer experiences. As a result, edge computing offers a practical solution that many businesses require.
Even though edge computing occurs locally, the cloud still plays a significant role. It retains historical data, provides additional processing capability, and facilitates communication among edge locations.
Regulatory Compliances
The regulatory compliance for automotive cybersecurity is evolving, as concerns about privacy and security for software-defined vehicles continue to develop. Here are a few noteworthy regulatory compliance measures:
- UNECE R155: OEMs must implement an efficient Cybersecurity Management System (CSMS) for risk identification and mitigation in all new vehicle classes.
- ISO/SAE 21434: The Society of Automotive Engineers (SAE) and the International Organization for Standardization (ISO) jointly developed organizational and procedural requirements to guarantee strong cybersecurity for automobiles at every stage of their lifecycle, from design to manufacture and operation to decommissioning.
- UNECE R156: UNECE Regulation 156 establishes the minimum cybersecurity and Software Update Management System (SUMS) requirements for vehicle manufacturers. According to the regulation, manufacturers must implement the SUMS and show that they have the procedures in place to meet all requirements for secure software updates.
- NHTSA Cybersecurity Best Practices for Modern Vehicles: The agency’s publication, “Cybersecurity Best Practices for Modern Vehicles,” outlined its non-binding recommendations for the automotive sector to enhance motor vehicle cybersecurity.
Challenges and their Use Cases in Software-Defined Vehicles
Here are some challenges and their use cases, which highlight the complexities involved in securing software-defined vehicles in today’s rapidly advancing automotive landscape:

Research Innovations in SDV Security
- Innovation 1: Novel semiconductor chip design with functional safety and cybersecurity capability for AI-ML-based software-defined zonal vehicle architecture
- Brief: A functional safety semiconductor chip design for automotive applications, focusing on AI/ML accelerator integration within Software-Defined Vehicle (SDV) architectures. It covers enhancements in real-time performance, ASIL-B compliance, and predictive fault detection. Key elements include fault tolerance through redundancy (e.g., N-Modular Redundancy), low-latency processing via ASICs, TPUs, and FPGAs, as well as robust cybersecurity to safeguard against vulnerabilities while ensuring adherence to safety standards. (Source)
- Assignee/University: AsteraLabs (ALAB)
- Application: Functional safety and cyber security in SDVs
- Value Proposition: Semiconductor chips designed with AI/ML to enhance vehicle performance, safety, and security, supporting the growth of fully autonomous, highly secure, and efficient vehicles.
- Innovation 2: Adaptive intrusion mitigation in software-defined vehicles using deep reinforcement learning
- Brief: A novel intrusion mitigation method that combines Advantage Actor-Critic (A2C) reinforcement learning with a Long Short-Term Memory (LSTM) network to detect anomalies and intrusions in V2X communications. The LSTM captures temporal patterns in V2X data to improve recognition of emerging threats, while the A2C model dynamically adapts defensive responses, such as flagging, blocking, or monitoring traffic based on changing threat conditions. (Source)
- Assignee/University: CISTER-ISEP
- Application: Intrusion Mitigation in SDVs
- Value Proposition: An intrusion mitigation method that combines Advantage Actor-Critic (A2C) reinforcement learning with a Long Short-Term Memory (LSTM) network to identify anomalies and intrusions in V2X communication systems.
- Innovation 3: Utilizing Generative Adversarial Networks (GAN) for Secure Communication in Software-Defined Vehicles
- Brief: GAN-based framework to create secure communication protocols for the dynamic environment of software-defined vehicles (SDVs). The generator is trained to produce communication sequences that closely resemble genuine, secure ones, while the discriminator identifies anomalies and potential vulnerabilities. Through iterative training, the system evolves to generate robust and resilient protocols. Simulation results show that this approach significantly reduces the success rate of cyber-attacks compared to conventional communication methods. (Source)
- Assignee/University: Danlaw Inc.
- Application: Communication protocol security in SDVs
- Value Proposition: 35% enhanced security in terms of attack detection and mitigation, with 20% reduction in communication latency, ensuring secure and efficient communication within SDVs.
- Innovation 4: Establishing trust between distributed services in a software-defined vehicle
- Brief: A multidimensional trust model for mutual validation and trust among distributed services within a computing system, specifically in a Software-Defined Vehicle (SDV), instead of relying on fixed secure identifiers. The model issues trusted identity tokens to establish trust both vertically, through a verifiable chain from the SDV’s hardware (e.g., a system-on-chip) to the software stack, and horizontally across distributed services within the system. (Source)
- Assignee/University: Google LLC
- Application: Distributed software services security in SDVs
- Value Proposition: A dual-layer trust structure enables more flexible and robust methods for verifying system integrity across components in the SDV.
Use Cases
Some use cases are given below:
| Company | Incident | Impact | Response |
| Tesla | In 2016, security researchers from the Keen Security Lab showed a hack in the Tesla Model S which could be exploited. They managed to hack into the vehicle’s system through a wireless connection and were able to manipulate steering, braking, and acceleration, among other things. | Although this hack was not malicious in nature, it was still dangerous as it exposed the vehicle’s communication systems and software to unprecedented threats. This raised new questions about the prospects of remote hijacking of self-driving cars and other autonomous systems. | With the help of an OTA update, Tesla remedied this issue almost immediately, demonstrating the effectiveness of OTA updates in enhancing security. |
| Kia | Security researchers discovered that Kia’s web portal enabled hackers to interact with their cars, including geolocating vehicles, locking and unlocking cars, starting cars, and activating features such as the horn. By entering the vehicle’s license plate number, attackers can gain access to the vehicle’s features. | The hack highlighted the risks of privacy and security that expose personal information and can exploit the bug to add themselves as a secondary user to the vehicle without the owner’s knowledge. | Researchers have developed an app that allows them to control the internet-connected functions of the vehicle. They also exploited these vulnerabilities to register as a dealer account on the Kia dealer portal. Once they had access to the dealer portal, they were able to reach the Kia dealer APIs, which gave them backend access to the system. From this point, the researchers took control of the affected vehicles. |
Key Solutions

VicOne’s xCarbon offers a frictionless on-board intrusion detection and prevention system for vehicles. Its highly configurable software-based solution is designed to provide OEMs and Tier 1 suppliers by enabling specific detection functions. It offers precise detection with expert-defined threat rules to minimize false alerts, customizable defenses, and automated edge-based threat detection and response. xCarbon provides complete control and streamlined lifecycle management, enabling frictionless self-defending smart vehicles through AI-driven edge detection. Acting as a Virtual Security Operations Center (VSOC) sensor, it sends telemetry data and system activity to detect and respond to threats, including identifying malicious CAN messages with abnormal IDs.
Recent Developments
- OneKey & ETAS developed a solution that improves vulnerability management in software-defined vehicles (SDVs) by integrating ETAS’s CycurRISK, a threat analysis and risk assessment (TARA) tool, with OneKey’s vulnerability detection capabilities. It streamlines the management of multiple vulnerabilities by providing developers with a prioritized and filtered list, enabling them to concentrate on the most critical areas for software enhancement. (Source)
- VicOne and Samsung Semiconductor formed a strategic partnership. Leveraging the use of Samsung Semiconductor’s Exynos Auto V920 System on a Chip (SOC) and VicOne’s next-generation intrusion detection and prevention system (IDPS), the collaboration seeks to transform cybersecurity in Software Defined Vehicles (SDVs). (Source)
Conclusion
Advancements in connectivity and embedded systems are accelerating the automotive industry’s transition toward software-defined vehicles (SDVs), where vehicle functions are increasingly decoupled from hardware and controlled via centralized, updatable software architectures.
Software increases the breadth and depth of a connected vehicle’s capabilities, but it also broadens the overall scope of a vehicle’s security requirements. Securing the data or hardware that the car uses to connect to other vehicles is no longer the only concern; protecting the car’s software is also crucial. Recently, many manufacturers have collaborated with various software providers to offer the kind of varied software-driven platforms that drivers seek. Due to this diversity, managing the multiple vendors and their unique tools and security procedures can be challenging. As software-based operations and features increase the number of connected entities and potential entry points in the automotive environment, a comprehensive approach to cybersecurity is particularly crucial.
Let's Take the Conversation Forward
Reach out to Stellarix experts for tailored solutions to streamline your operations and achieve
measurable business excellence.



