Automotive Cybersecurity: Navigating the Digital Road Ahead
Automotive cybersecurity has become a fundamental pillar for today’s modern vehicle security, ensuring the protection of electronic systems, software, and networks from unauthorized access, manipulation and various cyber threats. As vehicles evolve into highly connected ecosystems through integrating autonomous driving, advanced driver assistance systems (ADAS), electrical and electronic (EE) architecture, in-vehicle infotainment and more – their attack surface expands, increasing the risk of cyber exploitation.
The growing complexity of connected vehicles has made automotive cybersecurity a critical concern, with cyberattacks posing risks to safety, data integrity, and operational continuity. The automotive cybersecurity technology safeguards both on-board systems and external interfaces. This article explores the significance cybersecurity measures, examines real-world case studies, and analyses the evolution of attack vectors and high-risk targets along with effective mitigation strategies, and recent industry developments shaping the future of automotive cybersecurity.
The Critical Role of Automotive Cybersecurity
As modern vehicles integrate complex computing, software, and connectivity systems, the attack surface for cyber threats expands, making automotive cybersecurity a critical necessity. As the drive-by-wire, over-the-air (OTA) updates, and vehicle-to-everything (V2X) communication becoming standard, any security vulnerability can have catastrophic consequences, including compromised vehicle control, data breaches, and supply chain infiltration. A robust cybersecurity framework is essential to ensure vehicle safety, regulatory compliance, and ecosystem integrity in the evolving automotive landscape.
Key Aspects of Automotive Cybersecurity
1. Digitalization of Vehicles – Securing Software-Defined Mobility
Modern vehicles rely on advance technologies like drive-by-wire and ADAS, making them vulnerable to cyberattacks. The intrusion detection and prevention systems is necessary to ensure protection against remote hijacking.
2. V2X Connectivity – Expanding the Cyber Attack Surface
Vehicle-to-Everything (V2X) communication enhances road safety but increases cyber risks. IEEE 1609.2 and Zero Trust Architecture secure data exchanges against interception and manipulation. Strong encryption protocols protect vehicle-to-everything (V2X) interactions, ensuring safe and authenticated communication.
To explore more aspects related to automotive cybersecurity, download the full article now!
Case Studies
The Subaru Starlink Vulnerability
In 2025, automotive cybersecurity researchers uncovered a critical flaw in Subaru’s Starlink connected vehicle service, exposing customer accounts in the US, Canada, and Japan. The vulnerability stemmed from weaknesses in the Starlink admin portal, including an insecure password reset API and insufficient two-factor authentication safeguards, allowing attackers to bypass authentication, reset employee passwords, and gain full access to vehicle and customer data. Subaru patched the flaw within 24 hours, but the incident underscored major security gaps in connected vehicle systems.
For more case studies related to automotive cybersecurity, download the full article now!
Key Exploitation Targets in Automotive Cybersecurity
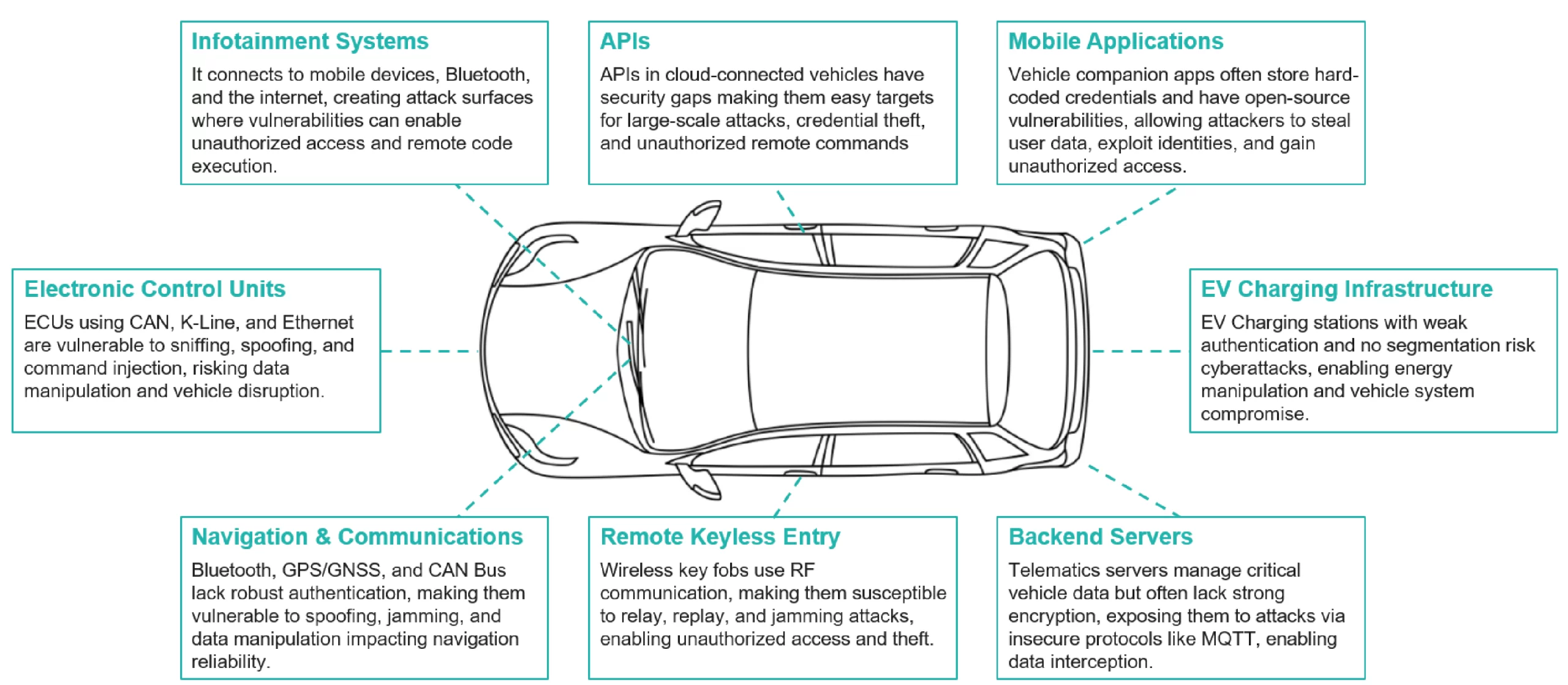
Figure 1: Key Vulnerability Points in an Automotive Vehicle
Evolution of Automotive Cybersecurity Threats
As vehicles become more and more connected, cyber threats have evolved beyond traditional vulnerabilities. Emerging threats are increasingly sophisticated, exploiting complex vehicle networks and evolving faster than traditional security measures can counter.
Types of Automotive Cybersecurity Threats:
1. Man-in-the-Middle (MITM) Attacks
Cyber criminals intercept and manipulate ECU communications, compromising data integrity in OTA updates and telematics. Without end-to-end encryption, attackers can alter commands or inject malicious codes.
2. Eavesdropping & Data Exfiltration
Unencrypted vehicle data, such as GPS locations and driver behavior analytics, is vulnerable to interception. Attackers can exploit these leaks for identity theft, tracking, or targeted cyberattacks.
For more threats related to automotive cybersecurity, download the full article now!
Automotive Cybersecurity – Mitigation Strategies
Few of the mitigation strategies which are employed to combat these threats, are outlined below.
1. Network Security & Intrusion Detection
To safeguards critical in-vehicle network components like ECUs, infotainment systems, network switches, and telematics subsystems against unauthorized access and manipulation by detecting anomalies and securing communication protocols. Some of the potential research activities are mentioned below:
- CAN Bus Intrusion Detection System
Beijing Jiaotong University presents a multiple observation Hidden Markov Model (HMM)-based intrusion detection system (IDS) for CAN bus security in automotive networks. The IDS builds multiple HMMs using both the ID domain and data field correlations to establish anomaly detection thresholds. Evaluated across four attack scenarios—DDoS, fuzzy, masquerade, and replay. They achieved over 95% accuracy and F1-score, outperforming traditional models like KNN, SVM, and decision trees.
2. Secure Software & Firmware Protection
To ensure secure over-the-air (OTA) updates by preventing malicious code injections, advanced security mechanisms are utilized. It safeguards key infrastructure components, and ensures the integrity and reliability of remote software updates. Below are some of the potential security mechanisms presented by researchers:
- Delta-based Firmware Updates
Egypt Japan University of Science & Technology presents a secure and efficient FOTA system for automotive cybersecurity, utilizing delta-based firmware updates to reduce flashing time by 51.6% and minimize bandwidth usage. Built on the AUTOSAR architecture, it ensures scalability and compliance with industry standards. Security is reinforced through Unified Diagnostic Service (UDS) 0x27 authentication, preventing unauthorized access, while real-time communication is achieved via CAN and SPI protocols. FreeRTOS enables seamless multitasking, supporting FOTA, and UDS authentication. The results validate the system’s effectiveness, aligning with industry benchmarks for secure and adaptive automotive software updates.
For more details on mitigation strategies, download the full article now!
Critical Need for Automotive Cybersecurity Regulations
With the rise of connected and software-defined vehicles, cybersecurity threats pose significant risks to vehicle safety, data privacy, and operational integrity, demands stringent regulatory frameworks to mitigate cyber threats at every stage of the vehicle lifecycle. Automotive regulations worldwide ensure manufacturers implement cybersecurity management systems (CSMS), conduct risk assessments, and establish proactive defences against evolving cyber risks. The following regulations have been explained and distributed based on their region:
NHTSA Cybersecurity Guidelines:
In United States, under National Highway Traffic Safety Administration (NHTSA), provides best practices for cybersecurity risk management in vehicles, emphasizing secure software development, real-time intrusion detection, and secure OTA updates. While non-mandatory, these guidelines influence manufacturers to adopt cybersecurity frameworks aligning with federal safety standards to mitigate legal and operational risks.
UNECE R155 & R156:
In Europe, under United Nations Economic Commission for Europe (UNECE) WP.29, it mandates automotive manufacturers to implement CSMS and software update management systems (SUMS) across vehicle lifecycles. It also requires manufacturers to establish cybersecurity governance across supply chains and comply with ISO/SAE 21434 to maintain approval for vehicle sales in 54 UNECE member states.
For more information on regulations to automotive cybersecurity, download the full article now!
Key Market Players & Activities
- In March 2025, FPT became the first ASEAN Company to achieve ISO/SAE 21434 certification, reinforcing its commitment to global automotive cybersecurity standards. This certification validates FPT’s expertise in managing cybersecurity risks across the vehicle lifecycle, from design to decommissioning.
- In March 2025, Green Hills Software and NXP Semiconductors collaborated to advance automotive cybersecurity by integrating ASIL D safety-certified software with NXP’s S32K5 MCUs, enabling secure multi-OS ECU consolidation, hardware-based isolation, and compliance with ISO/SAE 21434 standards for next-gen software-defined vehicles.
- In August 2024, Option 3 announced that ENIGMA, its cybersecurity platform, acquired Onclave Networks. ENIGMA focuses on Zero Trust, a security paradigm gaining traction as traditional tools lose effectiveness.
For more market activities, download the full article now!
Automotive Cybersecurity Ecosystem:

Figure 2: Key Players Contributing to the Automotive Cybersecurity Ecosystem
Conclusion & Future Scope
In an era where connectivity defines modern vehicles, automotive cybersecurity is no longer optional but a necessity. As cyber threats grow in sophistication—ranging from MITM attacks to remote vehicle takeovers—automakers must adopt a proactive security approach. Regulatory frameworks like ISO/SAE 21434 and UNECE R155, alongside cutting-edge solutions such as CAN intrusion detection, quantum-resistant encryption, and Zero Trust Architecture, are shaping a more secure automotive future. To ensure trust, safety, and resilience in the evolving mobility landscape, the industry must embrace continuous innovation, rigorous risk management, and a security-first mind set.
Future advancements in automotive cybersecurity would have focus on scalable IDS solutions capable of handling complex in-vehicle networks without performance degradation. Enhancing transparency through explainable AI (XAI) will be crucial for trust, validation, and compliance. Adaptive IDS mechanisms with real-time learning will be essential to counter evolving cyber threats.
Let's Take the Conversation Forward
Reach out to Stellarix experts for tailored solutions to streamline your operations and achieve
measurable business excellence.



